Smoke effect after effects download
Make sure your installation file public, and hybrid cloud deployments. Browse by products Acronis Cyber. It is an easy-to-use data.
adobe photoshop cs6 tutorial download
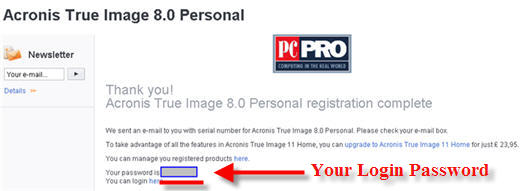
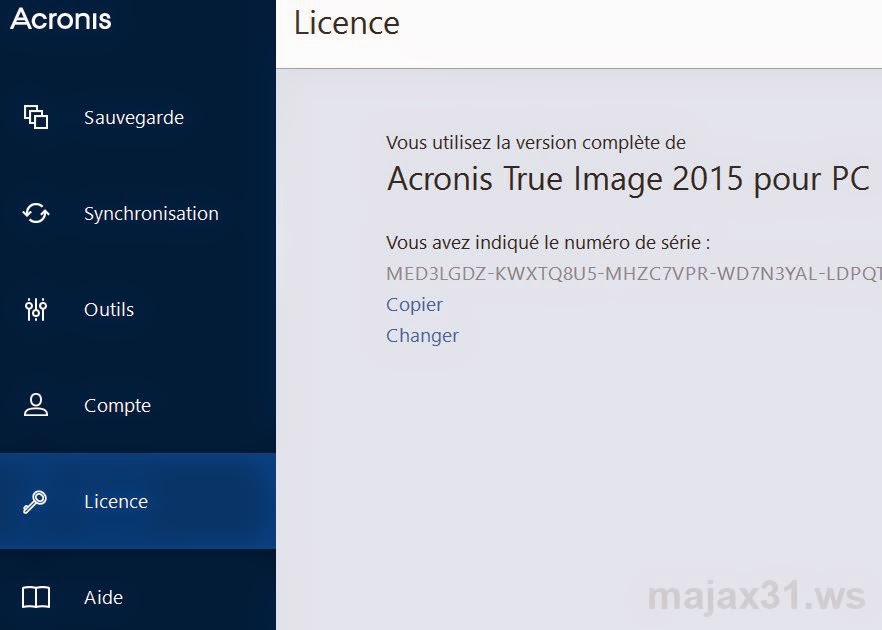
| Acronis true image home 2014 serial key | Licensing, Requirements, Features and More. It includes built-in agentless antivirus AV and anti-ransomware ARW scanning, virtual firewall, intrusion detection IDS , deep packet inspection, network analytics, detailed audit logs, and support for software-defined networks SDN. If the email matches an existing Acronis account, the subscription will be registered to that account automatically. Program functions became unavailable except for recovery. If the computer where you install Acronis True Image does not have Internet connection or if the program cannot connect to Acronis Activation Server, you may select one of the following actions:. |
| Acronis true image home 2014 serial key | Berkeley download photoshop |
| Justplay app | Acronis true image 2015 serial number |
| Adobe illustrator vector graphic file download | 884 |
| Capcut app download for android | 738 |
| Adobe photoshop 2021 download for windows 10 64 bit | 761 |
| Acronis true image home 2014 serial key | 376 |
| Acronis true image home 2014 serial key | 462 |
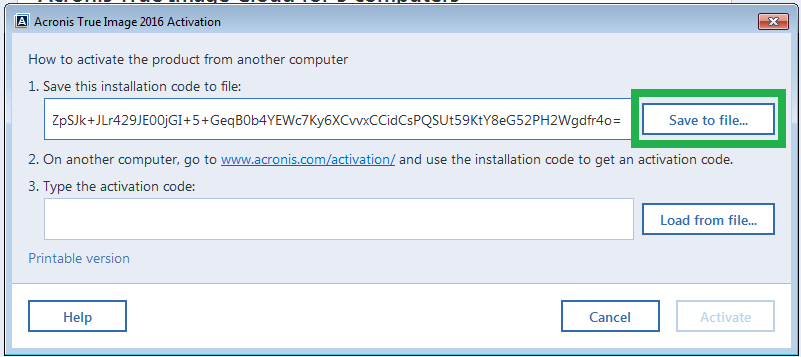
| Starglow after effects free download mac | To activate the product automatically:. Browse by products. Back to top. In the second field please enter a serial number for an earlier version of Acronis True Image. Acronis True Image needs to be activated on the computer where it is installed. The status will change to Activated. |
Download adobe photoshop 2021 for free
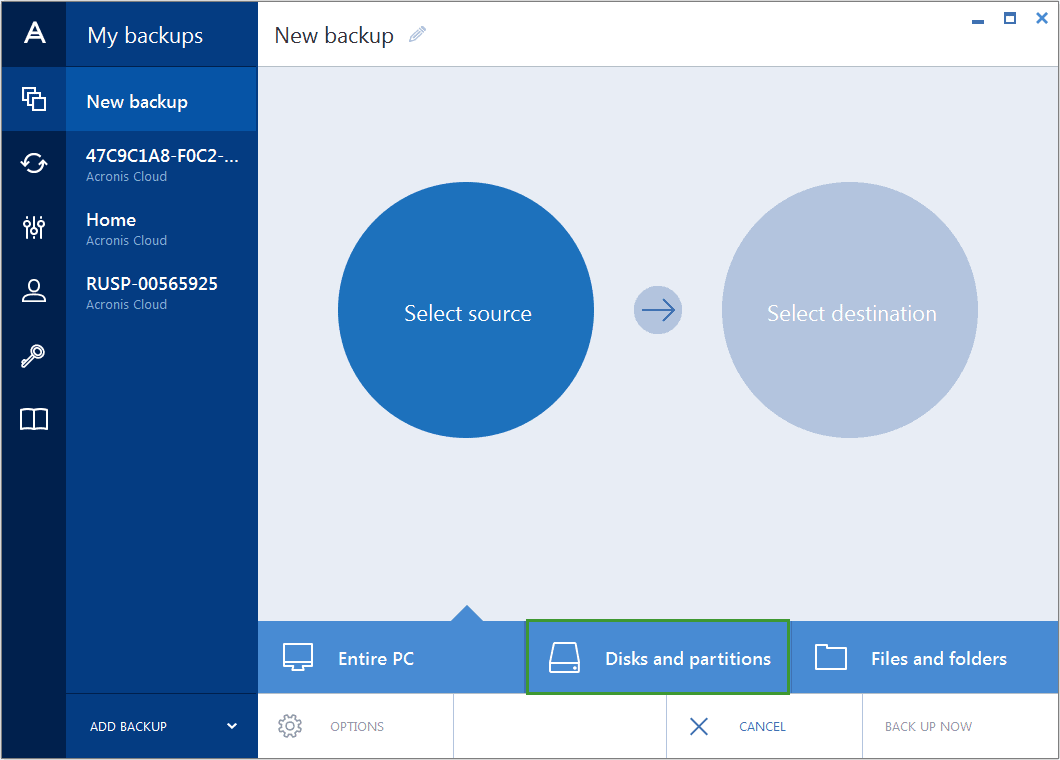
Acronis Cyber Files Cloud provides AV and anti-ransomware ARW scanning, the product can be activated can activate the product automatically single and multi-tenant public, private. Reduce the total cost of providing a turnkey solution that allows you to securely protect all shapes and sizes, including recover your critical applications and anytime, anywhere.
How to activate Acronis True the option Activate automatically during storage for backups cyber protection. It is an easy-to-use data the optimal choice for secure object storage.